System for Cross-domain Identity Management (SCIM)
Liferay DXP 2024.Q1+/Portal GA112+
System for Cross-domain Identity Management or SCIM, is an open standard that automates user provisioning. In other words, it’s a standard way to create, update, and deactivate user identities. SCIM provides a unified, RFC-compliant way to keep user/group data in sync between different applications. It consists of
- A defined schema for representing users and groups. See User Resource Schema and Group Resource Schema for more information.
- A RESTful API to run CRUD operations on those users and groups to keep them in sync. See SCIM User API Basics and SCIM Group API Basics for more information.
SCIM was released behind a beta feature flag in Liferay DXP 2024.Q1 and then moved to a release feature flag (LPS-96845) in Liferay DXP 2024.Q4. It was made generally available in Liferay DXP 2025.Q1/Portal GA132.
Using SCIM, you can automate the exchange of user identity information between your company’s applications and service providers like Liferay securely. This is useful if your company uses multiple applications and wants to keep user data in sync without custom implementations.
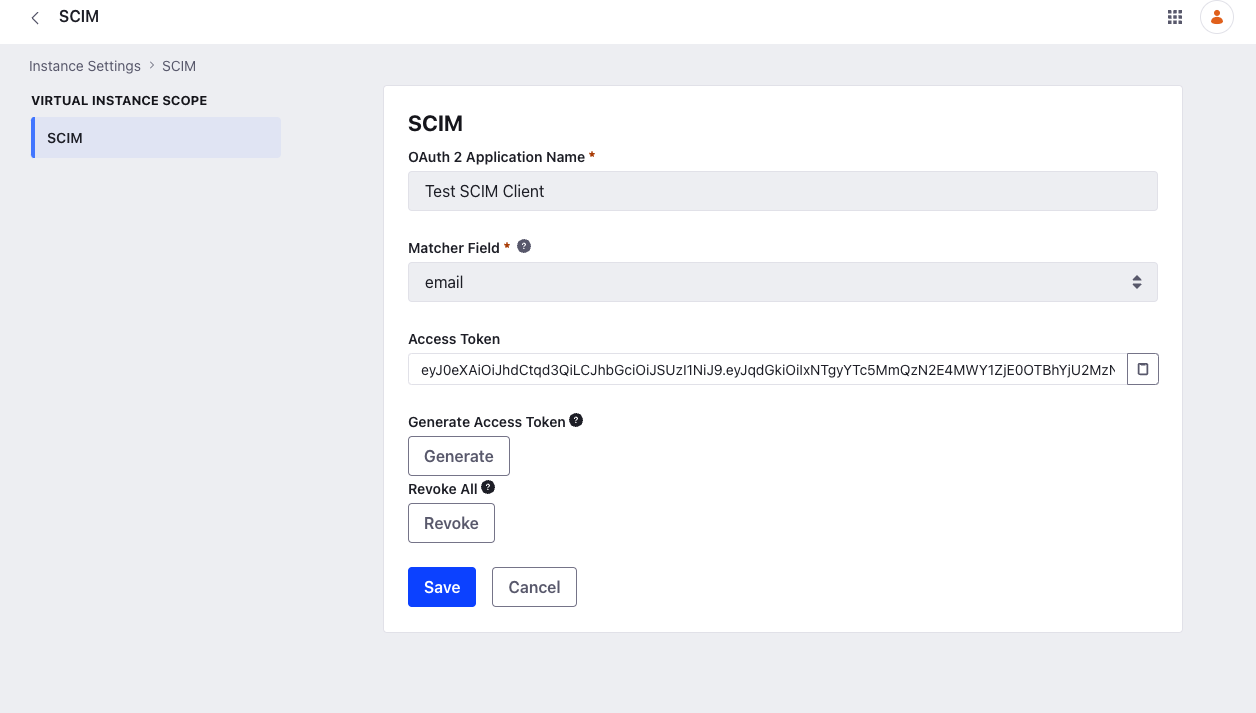
Registering a SCIM Client
-
Open the Global Menu (
 ) and navigate to Control Panel → Instance Settings → Security → SCIM.
) and navigate to Control Panel → Instance Settings → Security → SCIM. -
Enter a name in the OAuth 2 Application Name field.
The name entered here is used to generate the SCIM client ID. This ID links users and groups with the SCIM client. If your SCIM client name is
Test SCIM Client, the generated SCIM client ID isSCIM_test-scim-client. -
Set the Matcher Field to
userNameoremail.The SCIM client uses this field to match the user data in the service provider and the connected application. This avoids issues with provisioning and prevents data duplication.
-
The Access Token field is empty at first. Click Generate and click OK to populate the field with an access token. An access token expires after 1 year unless revoked. If this is not the first time you’re generating an access token, it overwrites the existing token, but it remains valid for at most 10 more days. You can use this grace period to configure the new token in the client application.
You can invoke the SCIM APIs by setting the access token in the
Authorizationrequest header. To revoke all access tokens, click Revoke and click OK. -
Click Save.
A scheduler runs daily to retrieve all OAuth 2 applications that start with the SCIM_ prefix. If the access token’s expiry is within 30 days, 10 days, or 1 day, all administrators are notified in Liferay and via email. A warning message also appears in the above page, instructing administrators to generate a new token before the expiry date.
After saving the SCIM configuration, an OAuth 2 application is provisioned. This app uses the Client Credentials flow and the currently logged in user becomes the default client credentials user. When generating a SCIM access token, this user becomes the owner of the generated token. All activity done using this token can be traced back to this user. You must ensure that you create or use an existing user with the appropriate permissions and privileges before saving your SCIM configuration. If you want to change the default SCIM user to a different one, see the steps below.
Changing the Default SCIM User
-
Open the Global Menu (
 ) and navigate to Control Panel → OAuth 2 Administration.
) and navigate to Control Panel → OAuth 2 Administration. -
Find the app based on the SCIM client ID generated earlier.
-
Scroll down to the Client Credentials User section and click Select.
-
Select a user with the appropriate permissions and privileges. If the user is already signed in, click Use Signed in User.
-
Click Save.
Resetting a SCIM Client
Liferay DXP 2024.Q4+/Portal GA129+ Beta Feature
To register a new SCIM client, you must reset the existing one to remove the SCIM client data and generated OAuth 2 token.
-
Open the Global Menu (
 ) and navigate to Control Panel → Instance Settings → Security → SCIM.
) and navigate to Control Panel → Instance Settings → Security → SCIM. -
Click Reset and then click OK.
This clears the following fields: Access Token, Matcher Field, and OAuth 2 Application Name. It also deletes the OAuth 2 application associated with the SCIM client.