Introduction
This recipe guides you through the basic steps needed to integrate PingOne, your Identity Provider (IdP), with your Liferay environment using Security Assertion Markup Language (SAML).
Prerequisites
PingOne environment
Liferay DXP environment
A user who has administrative access to PingOne environment
A user who has administrative access to Liferay's Control Panel
Steps
Sign in to your PingOne environment.
On the left sidebar menu, go to Applications → Applications.
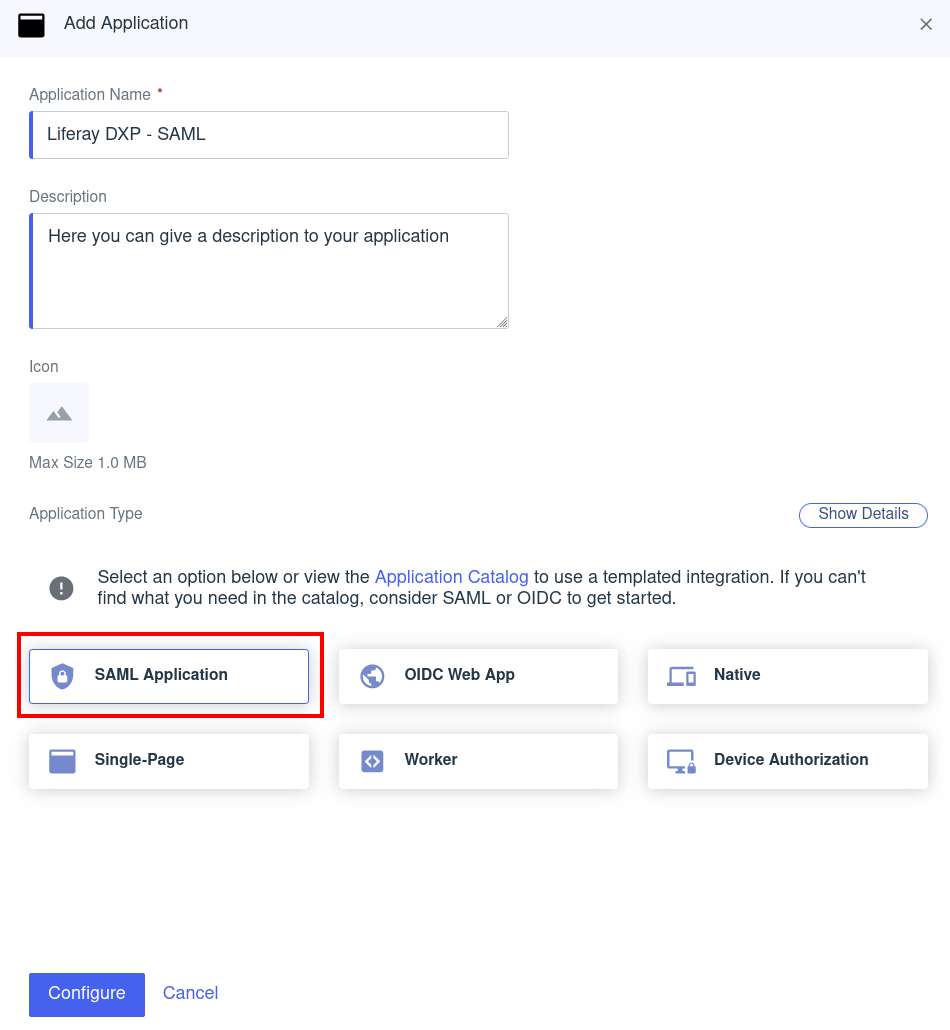
Click the Add button to create a new application.
Enter these values and click Configure:
Field Value Application Name Liferay DXP - SAMLDescription (Optional) Icon (Optional) Application Type SAML Application Under SAML Configuration, enter your application metadata and click Save.
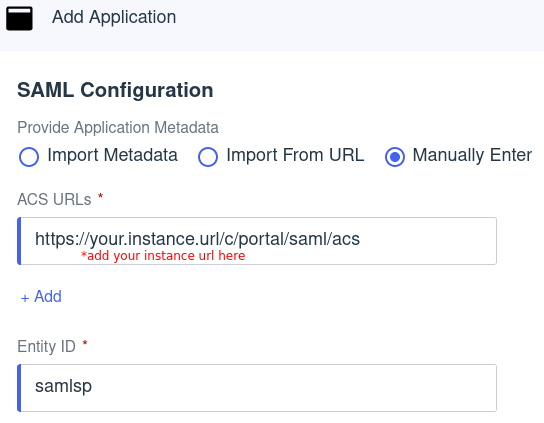
Field Value Provide Application Metadata Manually Enter ACS URLs https://[your_web_server]/c/portal/saml/acsEntity ID samlspGo to Configuration and click the Edit icon.
Enter these values and click Save:
Field Value Signing Certificate Choose between
Sign ResponseorSign Assertion & Responseaccording to your use case.See Defining signature policy (SAML) from PingOne to learn more about these choices.
Signing Algorithm RSA_SHA256Encryption Unchecked SLO endpoint https://[your_web_server]/c/portal/saml/sloSLO binding HTTP POSTAssertion validity duration (in seconds) 3000Go to Attribute Mappings, add these attributes, and click Save:
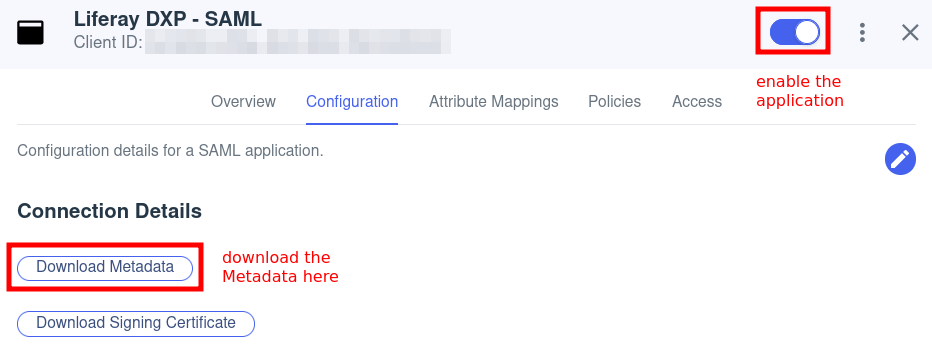
Attributes PingOne Mappings saml_subject Email Address emailAddress Email Address firstName Given Name lastName Family Name screenName User ID Go to Configuration, and download the Metadata XML file.
You will use it in a later step to configure Liferay DXP.
Click the toggle switch in the top right corner to enable the application.
Now configure Liferay DXP: On your Liferay DXP instance, open the Global Menu and go to Control Panel → Security → SAML Admin.
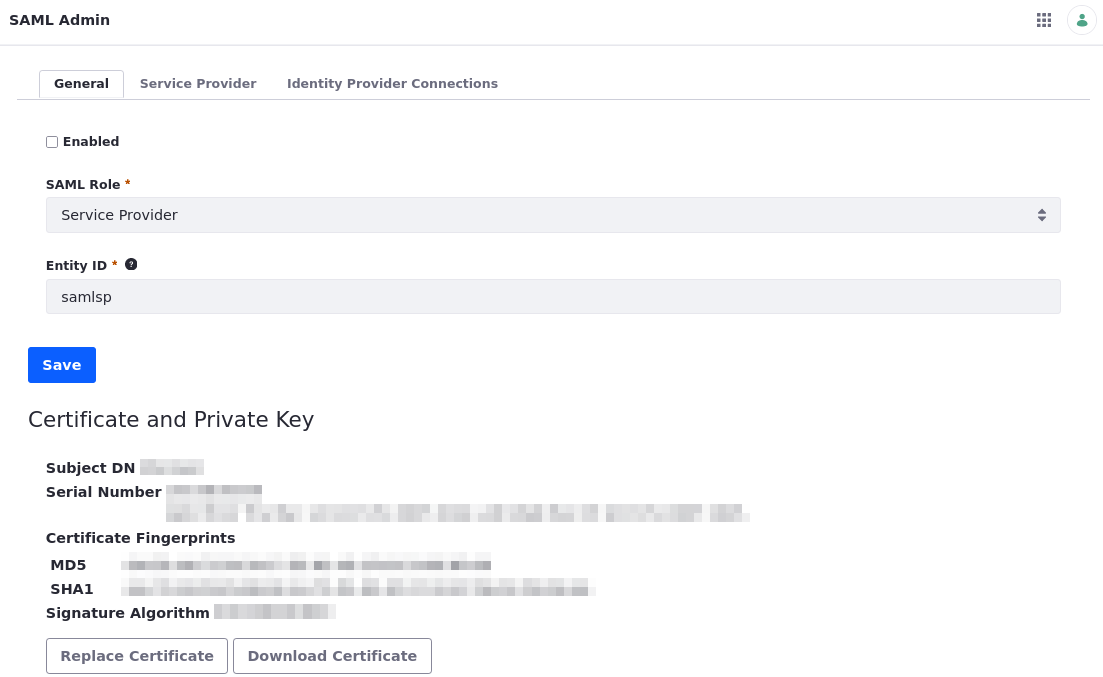
Under the General tab, set these values and click Save:
Field Value SAML Role Service Provider Entity ID samlspCreate a Certificate and Private Key. An Encryption Certificate is not needed.
Go to the Service Provider tab, ensure these settings are checked, and click Save:
-
Sign Authn Requests?
-
Sign Metadata?
-
SSL Required
-
Allow showing the login portlet.
-
Enable “Require Assertion Signature?” if you chose the
Sign Assertion & Responseconfiguration option in PingOne.
-
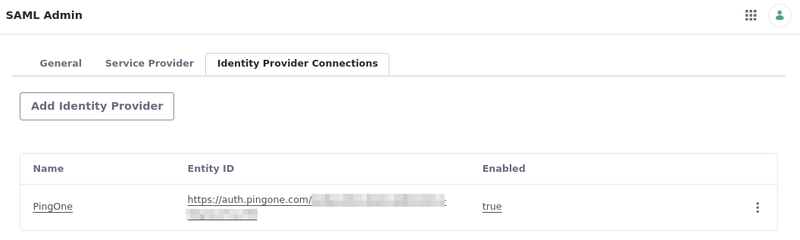
Go to the Identity Provider Connections tab.
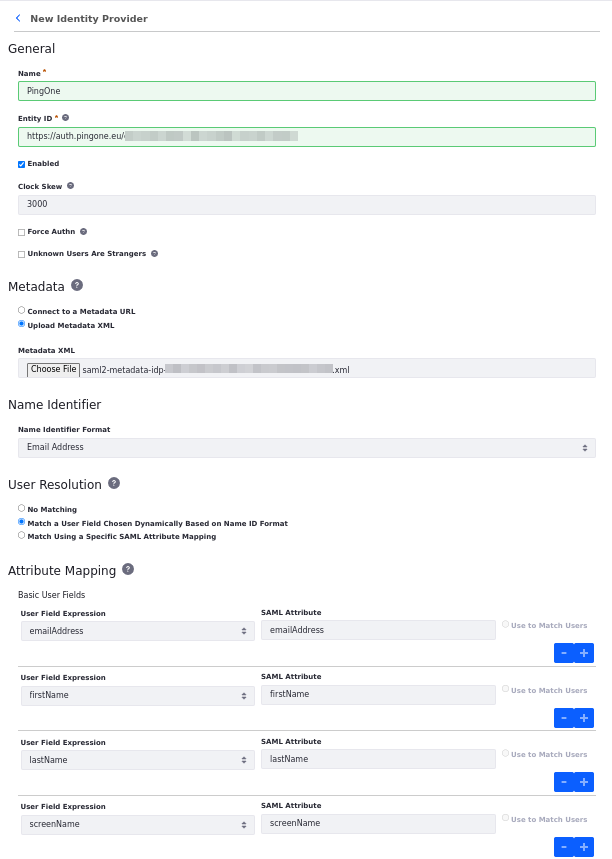
Click Add Identity Provider and configure these settings:
Field Value Name PingOneEntity ID Enter the entityIDfound in the Metadata XML file you downloaded from PingOneEnabled Checked Upload Metadata XML Checked Metadata XML Upload the Metadata XML file Name Identifier Format Email Address Under Attribute Mapping, add these Basic User Fields:
User Field Expression SAML Attribute emailAddress emailAddressfirstName firstNamelastName lastNamescreenName screenNameClick Save.
Go back to the General tab, check
Enabled, and click Save.You can now use PingOne with SAML to authenticate in your Liferay instance.
To validate your configuration: Log out of your current user.
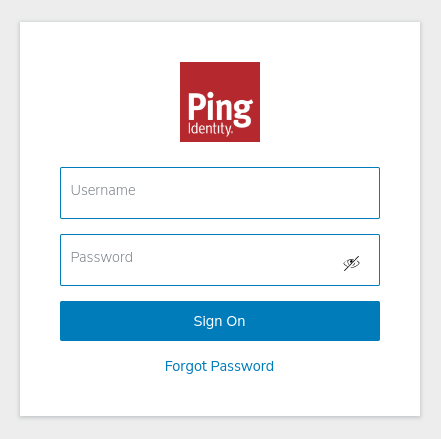
Click Sign In.
This redirects you to PingOne's login page.
Type in the user name and password for your user.
Once you've successfully logged in, your PingOne user should be registered in Liferay.
Sign back in as your Liferay admin user.
Open the Global Menu and go to Control Panel → Users and Organizations. Verify that your PingOne user displays on the list.

Do not enable SAML until you have finished configuring all settings.


Conclusion
Congratulations! Users may now authenticate to your environment using PingOne.
Tips
INVALID_ACS_URL
If you encounter ErrorCode: INVALID_ACS_URL, verify that your ACS URLs are configured correctly in PingOne with the appropriate path and Hypertext Transfer Protocol (HTTP or HTTPS). You can find them in your PingOne account by navigating to the application you created → Configuration tab → Edit icon.