Will Liferay DXP 7.1 support X-Frame-Options, X-XSS-Protection, X-Content-Type-Options headers?

Written By
Sivakumar Perumal
How To articles are not official guidelines or officially supported documentation. They are community-contributed content and may not always reflect the latest updates to Liferay DXP. We welcome your feedback to improve How To articles!
While we make every effort to ensure this Knowledge Base is accurate, it may not always reflect the most recent updates or official guidelines.We appreciate your understanding and encourage you to reach out with any feedback or concerns.
Legacy Article
You are viewing an article from our legacy "FastTrack"
publication program, made available for informational purposes. Articles
in this program were published without a requirement for independent
editing or verification and are provided"as is" without
guarantee.
Before using any information from this article, independently verify its
suitability for your situation and project.
Issue
- Will Liferay DXP 7.1 support X-Frame-Options, X-XSS-Protection, X-Content-Type-Options headers? If yes, how to enable the same.
Environment
Resolution
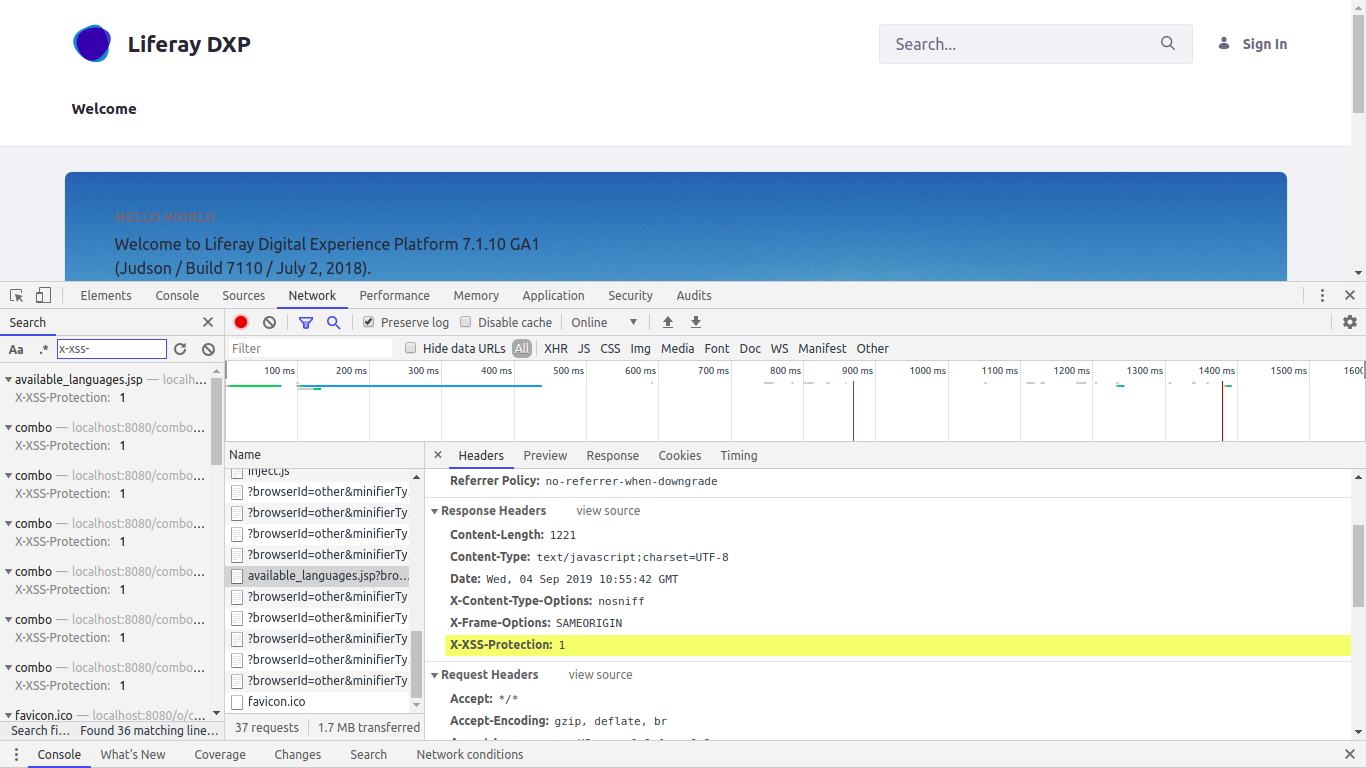
- Liferay DXP 7.1 is already secured with the following headers and it is enabled by default.
-
These values are found in the system.properties file (and not the portal.properties file) located inside the portal-impl.jar.
#
# Set this to true for the portal to send the "X-Frame-Options: DENY" HTTP
# header to protect against clickjacking.
#
# Custom HTTP header values instead of "DENY" can be specified per URL via
# the properties "http.header.secure.x.frame.options.*".
#
http.header.secure.x.frame.options=true
#
# Set this to nonempty value for the portal to send the "X-XSS-Protection"
# HTTP header to block cross-site scripting attacks. Possible nonempty
# values are "0", "1" and "1; mode=block"
#
http.header.secure.x.xss.protection=1
#
# Set this to true for the portal to send the "X-Content-Type-Options:
# nosniff" HTTP header to protect against MIME sniffing. Custom URLs can
# specified in the property
# "http.header.secure.x.content.type.options.urls.excludes" that allow for
# unhindered MIME sniffing.
#
http.header.secure.x.content.type.options=true
- To override the default settings, the best practice is to create a system-ext.properties file and never modify the system.properties directly.
-
Place the system-ext.properties file inside the ../ROOT/WEB-INF/classes folder. A server restart is necessary to apply the changes.
Did this article resolve your issue ?

