Issue
- The following headers are missing in Liferay:
- Missing ”X-Content-Type-Options” header
- Missing ”X-XSS Protection” header
- Missing ”X-Frame-Options” header
- Missing ”Content-Security-Policy” header
- Missing ”Strict-Transport-Security” header
- Missing cross-origin resource sharing(CORS)
- Missing ”Public-Key-Pins” header
Environment
- Liferay DXP 7.0-7.3
Resolution
-
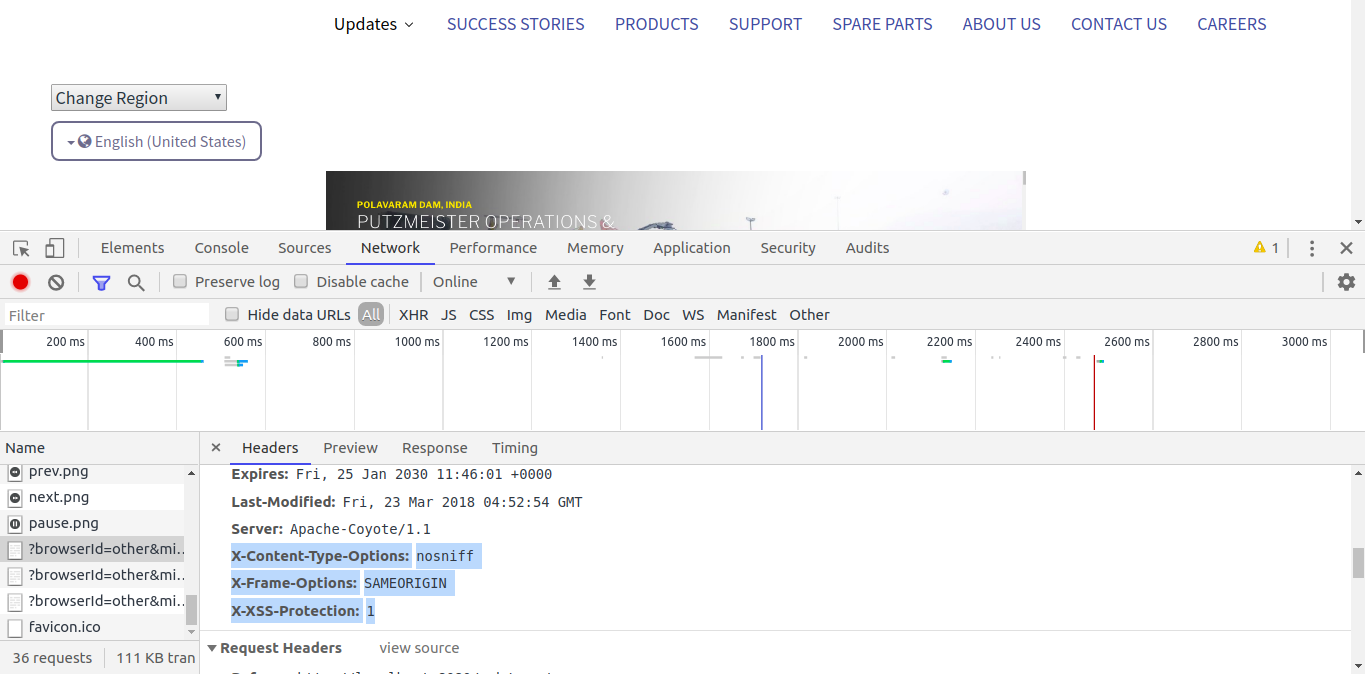
The following headers are available by default when inspected any of the requests.
- "X-Content-Type-Options" header
- "X-XSSProtection" header
-
"X-Frame-Options" headers
-
For the rest of the headers:
- "Content-Security-Policy" header: Liferay Portal doesn't directly support CSP in the sense that there's no configuration / UI for setting CSP directives. However, the CSP directives can be added on your own (eg, via your web server, theme). The Content Security Policy (CSP) article might help to achieve this.
- "Strict-Transport-Security" header: This configuration should be performed on Application Server like Tomcat (and not on Liferay) side. Enabling HTTP Strict Transport Security (HSTS) article may help to achieve this.
-
"Cross-origin resource sharing (CORS)"header: The Cross-Origin Resource Sharing is not managed by any Liferay configuration. The below articles have some helpful information and examples of web server configurations that can be used to enable CORS.
- Cross-Origin Resource Sharing (CORS)
- CORS Filter
- Note: The CORS configuration can be set within Liferay since DXP 7.2. Please refer to the documentation Configuring CORS for 7.2 and Setting Up CORS for 7.3.
- "Public-Key-Pins" header: This configuration should be performed at web server. This article: HTTP Public Key Pinning (HPKP) might help in enabling the Public-key-pins.
Additional Information
Please Note: The above hyperlinked articles are unofficial articles that are shared to basic information. Your use of those articles is completely at your discretion.
The headers described from 4 to 7 should be configured either at the application server or at the web server and both the platforms fall beyond the scope of Liferay Support.
