紹介
This recipe guides you through the steps to integrate Okta, your Identity Provider (IdP), with your Liferay environment using OpenID Connect.
prerequisites
Okta Dev account
Liferay DXP environment
Administrative access to Okta Admin Console
Administrative access to Liferay's Control Panel
steps
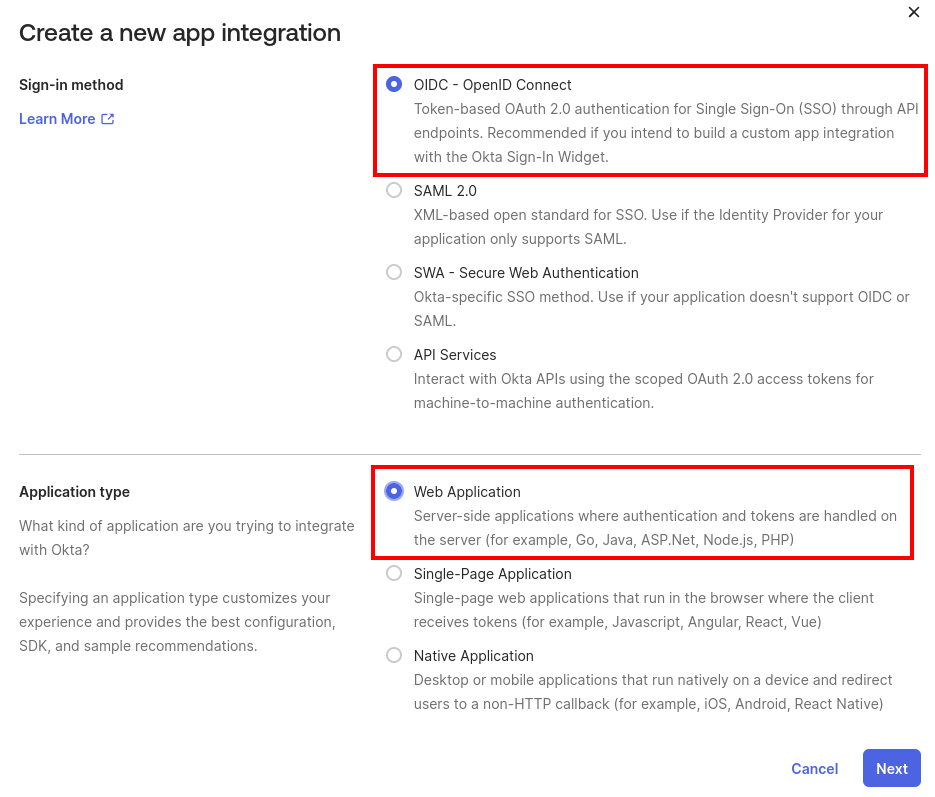
Log in to Okta Dev and navigate to Applications → Add Application → Create App Integration.
Select OIDC - OpenID Connect, under Sign-in method, and Web Application, under Application type.
Enter Liferay DXP - OIDC as the app integration name.
For grant types, select Authorization Code and Refresh Token.
Enter
https://[your_instance_url]/c/portal/login/openidconnectfor the sign-in redirect URIs.Enter
https://[your_instance_url]for the sign-out redirect URIs.Under assignments, select Skip group assignment for now.
Click Save.
On the Assignments tab, assign users to this application.
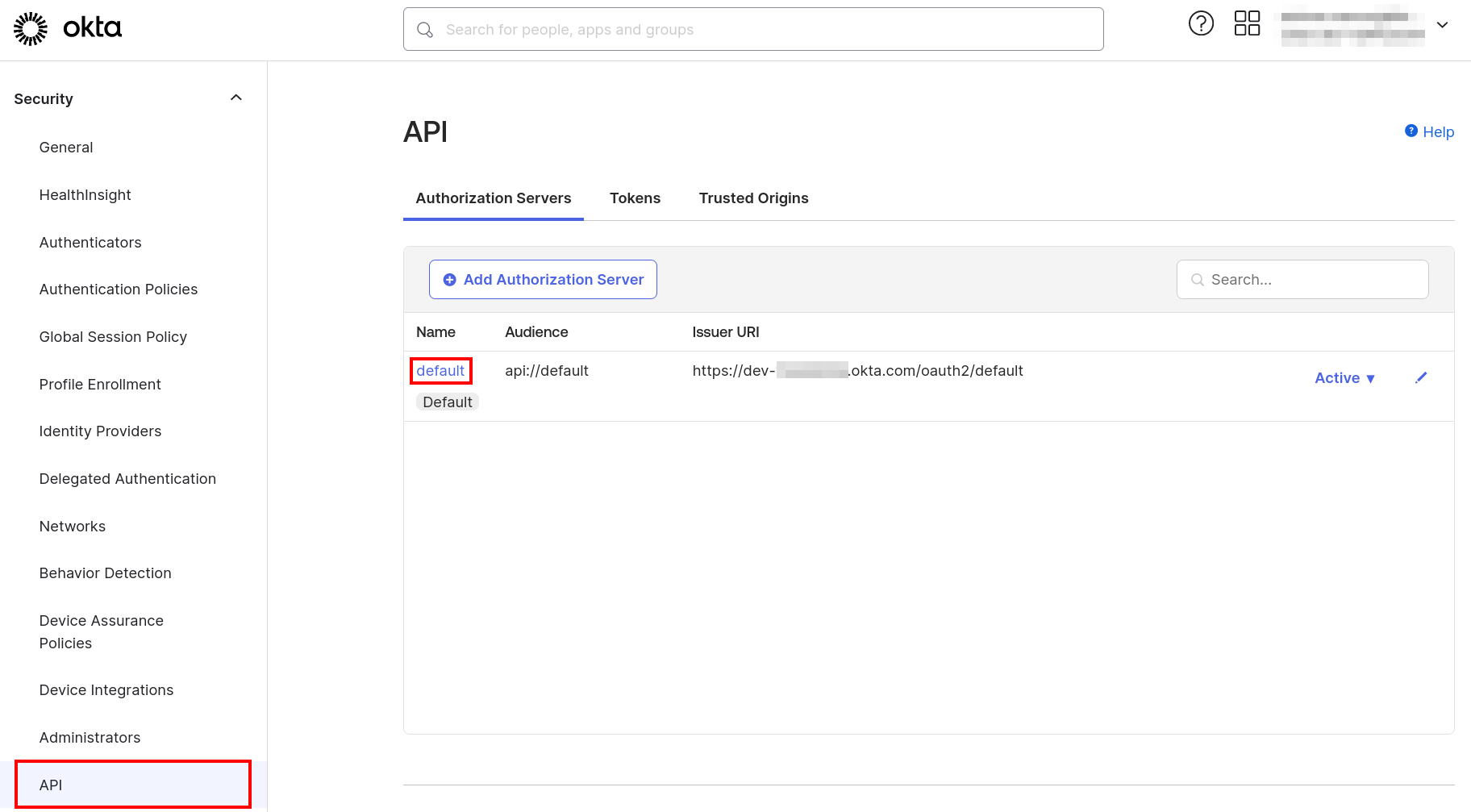
Now obtain the endpoint URLs: In your Okta Dev account, go to the side panel and navigate to Security → API.
Under the “Authorization Servers” tab, locate the server named
defaultand click on it to edit its configuration.Click on the "Metadata URI" link, which typically looks like this:
https://dev-123456.okta.com/oauth2/default/.well-known/oauth-authorization-server. Here are examples:This will give you the necessary URLs, with the exception of /userinfo endpoint. You can construct that endpoint by combining your base URL with the Auth Server name. For example:
https://dev-123456.okta.com/oauth2/default/v1/userinfo.Now configure the Liferay DXP instance: On your DXP instance, navigate to Global Menu → Control Panel → Instance Settings → Security → SSO.
Go to the OpenID Connect Provider Connection tab and add a new connection entry.
Fill in the fields with the data you find at the endpoint URLs, as shown in the table below.
Field Data Provider Name Okta OIDC Scopes scopes_supportedAuthorization Endpoint authorization_endpointurlIssuer URL issuerurlJWKS URI jwks_uriurlSubject Types subject_types_supportedToken Endpoint token_endpointurlUser Information Endpoint Combine your base URL with the Auth Server name. For example: https://dev-123456.okta.com/oauth2/default/v1/userinfoOpenID Connect Client ID Under your application's General tab in Okta OpenID Connect Client Secret Under your application's General tab in Okta Enable OpenID Connect: Navigate to Global Menu → Control Panel → Configuration → Instance Settings.
Click on SSO under the security section.
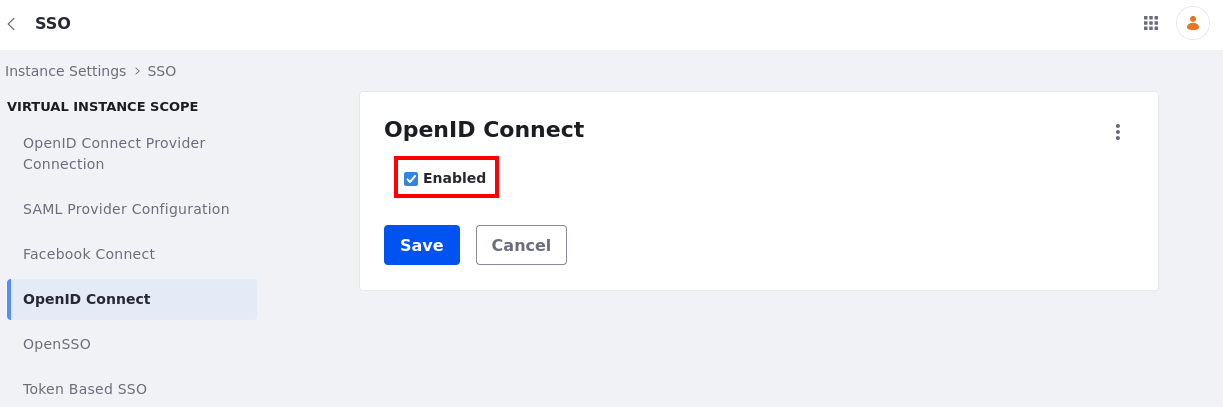
Go to the OpenID Connect tab, click the Enabled checkbox and click Save.
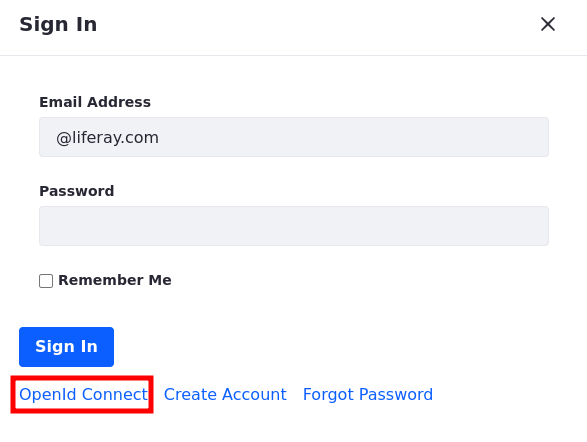
To validate the configuration, in your Liferay DXP instance, click on the Sign In button and choose OpenId Connect.
Choose Client to Okta OIDC from the list.
You are redirected to sign in to Liferay DXP using your Okta account.
Make sure to assign yourself and provision your own user account so that you will still be able to log in as the Liferay administrator.
By default, Liferay DXP requires new users verify their email address upon first login. This requires Liferay DXP to have a configured connection to a mail server, in order to send the verification emails. To disable this requirement navigate to Control Panel → Instance Settings → Platform → User Authentication and unselect the checkbox for "Require strangers to verify their email address”.

conclusion
Your Liferay installation now supports authentication using Okta and OpenID Connect!
ヒント
Sign-in and Sign-out Redirect URIs
If you encounter a "400 Bad Request" error, verify that your sign-in and sign-out redirect URIs are configured correctly in Okta with the appropriate path and Hypertext Transfer Protocol (HTTP or HTTPS). You can find them in your Dev Okta account by navigating to the application you created → General tab → General Setting → Login section.